- Author Lauren Nevill nevill@internetdaybook.com.
- Public 2024-01-11 01:05.
- Last modified 2025-01-23 15:15.
Often, a person who downloads, for example, a new template or plugin for the CMS of his site, finds himself in an unpleasant situation: after installing the template, advertising spam links suddenly appear on his site. They may not be visible, but hidden from the user's eyes. But they are clearly visible to the search robot. And this unwanted advertising has a negative impact on the site's ranking and the search engine's trust in it, which means that the site will be lower in search results than it could have been. Let's figure out how to clean your site from unwanted extraneous code.

Necessary
- - Own website on one of the popular CMS - Joomla, WordPress or others;
- - a computer connected to the Internet.
Instructions
Step 1
First, you need to determine where in the page code the extraneous ads are displayed. To do this, open our website in the browser on the page where there is suspicion of the presence of unwanted code. If someone else's code came to you from an established template, then most likely spam ads will not be on the main page, but on the internal pages of the site.
Open the source code of the site (in most browsers this is done using the Ctrl + U keyboard shortcut). The quickest way is to search for the https:// combination in the source code, since advertising is always links. If you find links that you did not post, then your fears were not in vain. Remember the identifier (id) or class (class) of the element in which the ad is placed.
Step 2
The next step is to download your site via FTP to your computer: search faster on your computer. When downloading, search for files that contain text with the name of the id or class that you defined earlier. It is convenient to search using the file manager of the type.
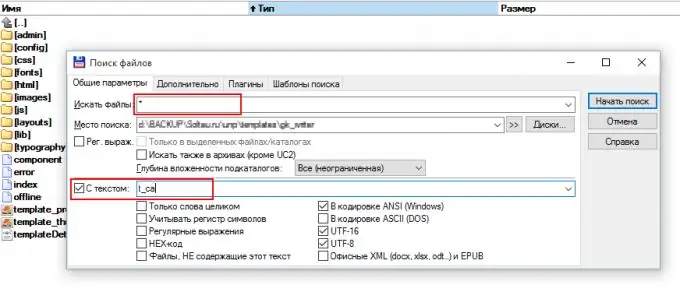
Step 3
It is possible that you will not find anything. This is not surprising, since attackers often obfuscate (encrypt) their code. And often a built-in PHP function called base64_decode is used for encryption. Therefore, the next thing you should do is to search the downloaded files with the base64_decode text. You will most likely find several php files with this function. Study them carefully. If the code that uses this function only encrypts something and then displays it on the page, then this is probably exactly what we are looking for. For example, there might be a construction similar to this:. The variable $ v can have any name. Make a backup copy of the file, and then delete all sections of the code where this construct occurs.
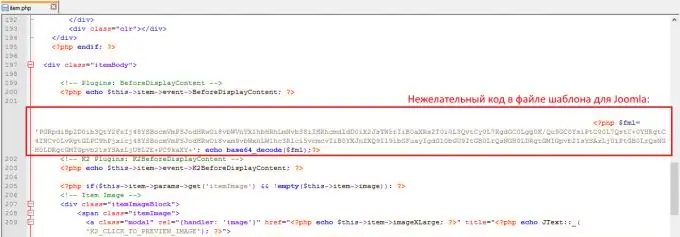
Step 4
Now upload the "cleaned" version of the file to the server. Make sure your site is working. If the site is working normally, and the advertising spam links have disappeared when viewing the source code, then everything has been done correctly. If the site gives an error, then replace the new file with the saved backup. There are two options: either it is not malicious code, or the code has some kind of self-defense function. In any case, you need to understand more deeply.
Step 5
See what files are used to build the page. To do this, insert the following code at the end of the template after the closing "/ html" tag:. This code will list the files that are involved in the creation of each page on your site. The unwanted code will be unambiguously in one or more files from this list. The list can be quite lengthy, but it will still limit your search.






