- Author Lauren Nevill nevill@internetdaybook.com.
- Public 2024-01-18 21:47.
- Last modified 2025-01-23 15:15.
Winlocker is a special type of malicious software from which an inattentive user of a personal computer and network is practically not immune.
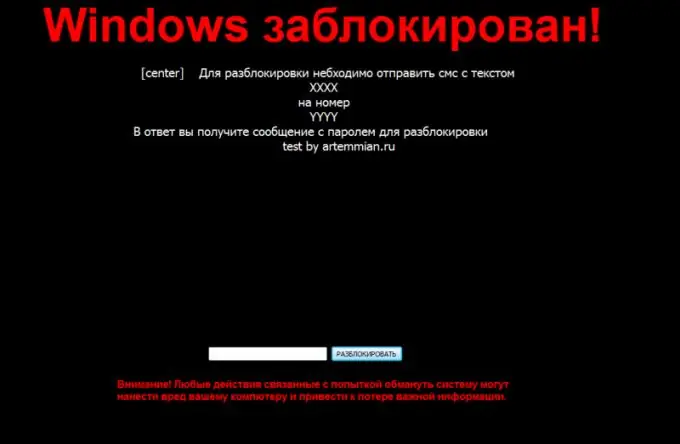
What is Winlocker?
Winlocker is a type of malicious software that blocks the user's operating system. Naturally, if this virus gets on the computer, it immediately starts doing its own thing. For example, after infection, it automatically registers itself in the system startup, which means that it automatically starts together with the personal computer. Once launched, Winlocker restricts the user from literally all actions with a computer mouse and keyboard. At the same time, he also asks to send a certain amount of money to the specified account, after payment of which it will supposedly be automatically deleted. Of course, if the user takes such a trick, no unlocking of the system will occur.
Winlocker mostly has the.exe extension. At the same time, it is usually distributed through various electronic messages, which in one way or another are of interest to the user. An attachment is attached to such a message, which can be either a picture or a video (although in fact it is the same Winlocker). In order not to fall for the trick, the user just needs to be vigilant and at least look at the extension of the file that was sent to him. Usually images have the following extension -.jpg,.pmg,.gif, etc. Videos, in turn -.avi,.mp4,.flv, etc. If the file extension does not match these extensions, it is most likely Winlocker (which extension is.exe).
How to remove Winlocker?
If this malicious software nevertheless penetrated your personal computer, you should first remove it from startup, and only then completely remove it from the PC. First, before proceeding with the removal, you should check which functions Winlocker has blocked. To do this, press the hotkey combination Ctrl + alt="Image" + Delete. If these steps did not work, then try starting the Run program using the Win + R combination and entering the regedit command.
It's worth noting that in most cases, none of these commands work. Then you should start the computer in safe mode (after restarting, press the F8 button). Further, the regedit command is also written on the command line and the registry editor is launched. Here you should go to the following branches: HKEY_LOCAL_MACHINE / SOFTWARE / Microsoft / Windows / CurrentVersion / Run and HKEY_CURRENT_USER / Software / Microsoft / Windows / CurrentVersion / Run. In these branches, you need to remove unfamiliar programs: hkcmd.exe, igfxtray.exe, igfxpers.exe. Next, you need to find the Shell and UserInit parameters, the value of which should contain explorer.exe and the path to the userinit.exe file (C: / Windows / system32 / userinit.exe), respectively.
Usually, instead of one of these parameters, the path to the malicious file is written. You need to remember it, and after the correct values are entered, go along this path, find the file and delete.






