- Author Lauren Nevill nevill@internetdaybook.com.
- Public 2023-12-16 18:48.
- Last modified 2025-01-23 15:15.
Many WhatsApp users are interested in privacy issues, and many are not interested in the protection of correspondence, but in how to read someone else's correspondence in WhatsApp remotely. What are the ways to read the correspondence and what is it for?

Browser use
The most effective and at the same time the easiest way is to use your computer's browser. In order to track another person's whatsapp using a browser, you need very little:
- person's phone;
- a computer with Google Chrome;
- a few seconds of free time.
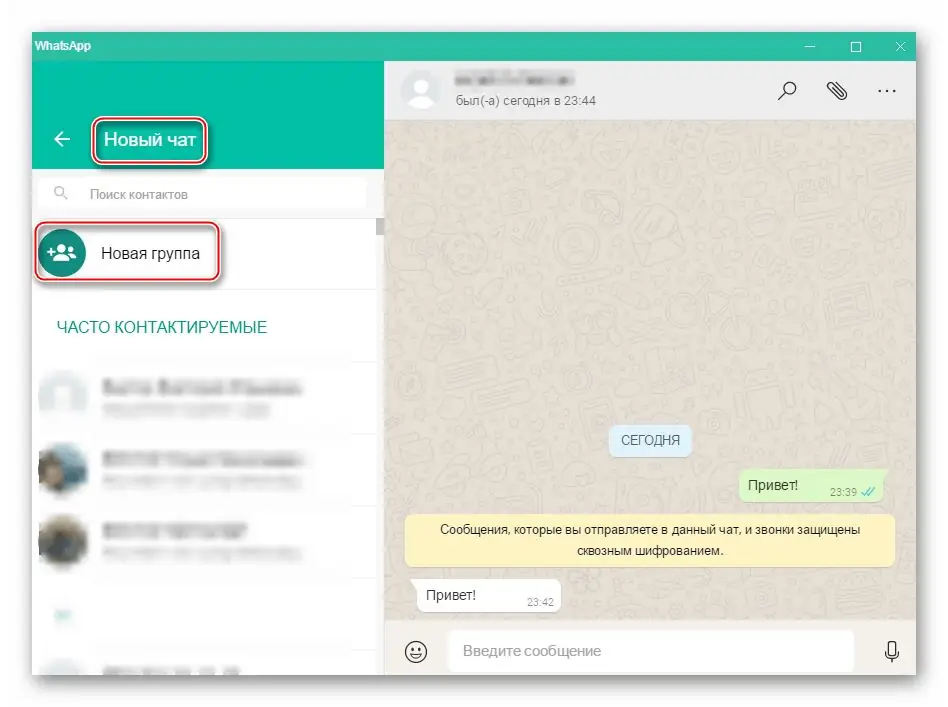
And you need to do the following:
- Go to the browser.
- Go to the internet resource web.whatsapp.com.
- Take the subscriber's phone, go to the WhatsApp application, then go to chats, then to the menu and to WhatsApp Web.
- Hover the gadget at the barcode and go to the chat.
But this method has the following disadvantages:
- the person whose correspondence needs to be read must be online;
- anyone is able to see if the “victim” is online. This can be seen by the person himself, so he can guess that his profile is being viewed;
- the method does not work if a person is sitting in the messenger via the iPhone.
You can also use mail.
Mail Usage
This method is suitable for any operating systems of mobile devices. You need to do the following:
- Open the program and go to chats.
- Select the chat you are interested in.
- Select the point of sending by e-mail.
- A mail will appear with a correspondence file.
- Send a letter with correspondence to your mailing address.
This method has several disadvantages:
- you cannot read the messages that appear after using this method;
- it will take a long time to send messages and cover your tracks;
- you need a constant Internet connection.
These two methods have one drawback - to complete them, you need to keep the phone of the person whose correspondence you need to read.

Simple conversation
If a person is new to computer programs or is simply afraid of complex passwords, you can use the simplest and fastest option. If the object of surveillance is a close or dear person and he uses the function of automatically saving passwords, you can either extract the password from him using leading questions, or wait for the person to enter the messenger.
In any case, having received a login and password by asking questions or by saving data while the "victim" is absent, a person is able to log into someone else's profile at any time and through any device and read all the correspondence that was done.
The most important thing to remember with this kind of surveillance is that the relationship between the “victim” and the “spy” can deteriorate. Therefore, it is important to weigh everything before such actions and be prepared for the consequences.
Spam software
If the method described above is mostly suitable for those who are poorly versed in computers, the spam program is suitable for those who know computers and understand at least something in programming. For them, using spambots would be a great way.
The essence of this action in the same way is to fish out the necessary information data required to enter the user profile. The only difference is that here the "spy" and "victim" do not meet in person and do not waste time asking questions. You can either write the program yourself or try to find it on the Internet.
The main job of a spam program is that after being installed on the victim's computer, it will read logins and passwords, as well as other user data. After that, she will send data to the specified e-mail, and the "spy" will only have to enter these data and read the correspondence.
Keylogger
There are some users who do not like any of the above methods, but the desire to find out the history of the correspondence still remains, you can use another spyware - keylogger. Of course, here, as in all other cases, the problem lies in the fact that the "spy" needs to install the appropriate software on the "victim" PC.
There is another important problem with this method - a program of the "Keylogger" type will send not only correspondence to the "spy" mail, but also a list of all sites visited by the "victim". It will send everything that the user clicked on and where the user entered.
The "spy", having collated all the received information data, will be able to determine the data input without any problems. However, the program will be of no use if the victim uses the generation and automatic saving of passwords on his computer. Indeed, in this case, the person will not enter his account data through the keyboard.

But there are also several advantages to this method. For example, the antivirus software used on the computer does not recognize the keylogger as a virus. In addition, keylogger is not visible in the list of programs installed on the computer, making it completely invisible to the owner of the device. And in order to remove this spy, in some cases it is only necessary to reinstall the operating system.
Internet intermediaries
There is always someone who wants to get the necessary data, while not risking anything and not spending a lot of their personal time on it. In this case, the use of qualified intermediary specialists who can track the correspondence can solve the problem.
All you have to do is find the right person who can get the data you need. They usually find and wait for orders on specialized sites.
When choosing this method, the observer in most cases does not need to do anything, just tell the performer his own e-mail address and all the data that is known about the victim.
In some cases, some other information may also be required from the person. After the actions between the "customer" and the "contractor" are agreed upon, the "customer" will only have to pay for the services and wait for the moment when the information appears in the mail.
Depending on the specifics of the order and the qualifications of the "executor", he can send the "customer" either a pair of login-password, or the entire correspondence with this pair.
The main advantage of this method is that no time or mental expenditure will be required from the "customer". But the main disadvantage is that you need to pay for services and sometimes it is a very large amount. But there is one more disadvantage, and it lies in the fact that the "executor" can be either a scammer, or he will simply "leak" information about the order to a potential "victim".
Instead of a conclusion: what to choose?
If we conclude on how to read someone else's correspondence in WhatsApp remotely, we can note that the "spy" will always have to sacrifice at least something. For example, if he uses specialized programs, this can lead to a complete loss of data, and if he turns to intermediaries, he can lose money.
The most optimal and safest way is to use a keylogger. You can also simply trick out the necessary information and use it. These are not entirely remote methods, but for those who want to get by with a little blood, they are suitable.
And again, it is necessary to weigh several times all the pros and cons of tracking the correspondence of another person in the WhatsApp messenger.






