- Author Lauren Nevill nevill@internetdaybook.com.
- Public 2023-12-16 18:48.
- Last modified 2025-01-23 15:15.
It will not be possible to convert the asterisks that you see in the browser to passwords for the simple reason that the passwords are not there. The browser makes a request for the page to the server, receives in response the source code of the page and displays everything sent. You can look at absolutely everything that the server sent and make sure that the password is not there in any form. But passwords hidden by unreadable icons in programs installed on the computer can be seen.
It is necessary
Any of the password decryption programs
Instructions
Step 1
Every computer user has forgotten any of his passwords at least once, so password recovery programs began to appear almost simultaneously with encryption programs. It would be no less absurd to include such a program in the standard delivery set of an operating system, one of the functions of which is to keep these same passwords safe, than to store salt and sugar in one jar. Therefore, you will not find such a program as part of your OS, but there will be no problems with this on the network. If you need to see your password hidden by asterisks, then the first step is to find it on the Internet and download the appropriate program. For example, it might be a program named Pass Checker.
Step 2
The program downloaded to the computer must be installed, but some of them do not require this either - it is enough to unpack the archive, and the program is ready to work. Pass Checker belongs to this group of applications - just double-click the Password.exe executable and the program is up and running.
Step 3
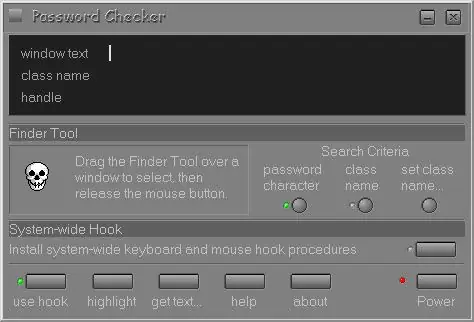
Now launch the application, the asterisks of which you want to decrypt. Further actions depend on the decoder program you have chosen. For example, in Pass Checker you need to drag the skull image with the left mouse button onto the field with decrypted asterisks.
Step 4
The skull cracks its jaws, after which the decoder program will display the password hidden by asterisks in the field labeled window text. From here you can copy it and use it further as you see fit. In other programs, the procedure will be different, but the principle will remain the same: the decoder must specify the object with unreadable characters that you are interested in, and then take the decoded result from the corresponding field.






